What is a Cyber Kill Chain and How It Helps in Threat Defense?
We are going to take one inch into what the Cyber Kill Chain is all about, the seven stages involved, and how it works in bulking cyber protection.
What is the Cyber Kill Chain?
Lockheed Martin came up with the Cyber Kill Chain, which is a guide that shows the usual steps by attackers to go through in order for an attack to succeed, like when someone wants to steal information or damage things. So, rather than just proving it out, it's really giving defenders a much better chance of cutting it short before it gets much worse.
There are thus seven steps from scoping the target into the last act whereby the attacker actually does something in the hacked system. The clearer it gets for an organization, the more surprise it will have when any blockage finally arrives.
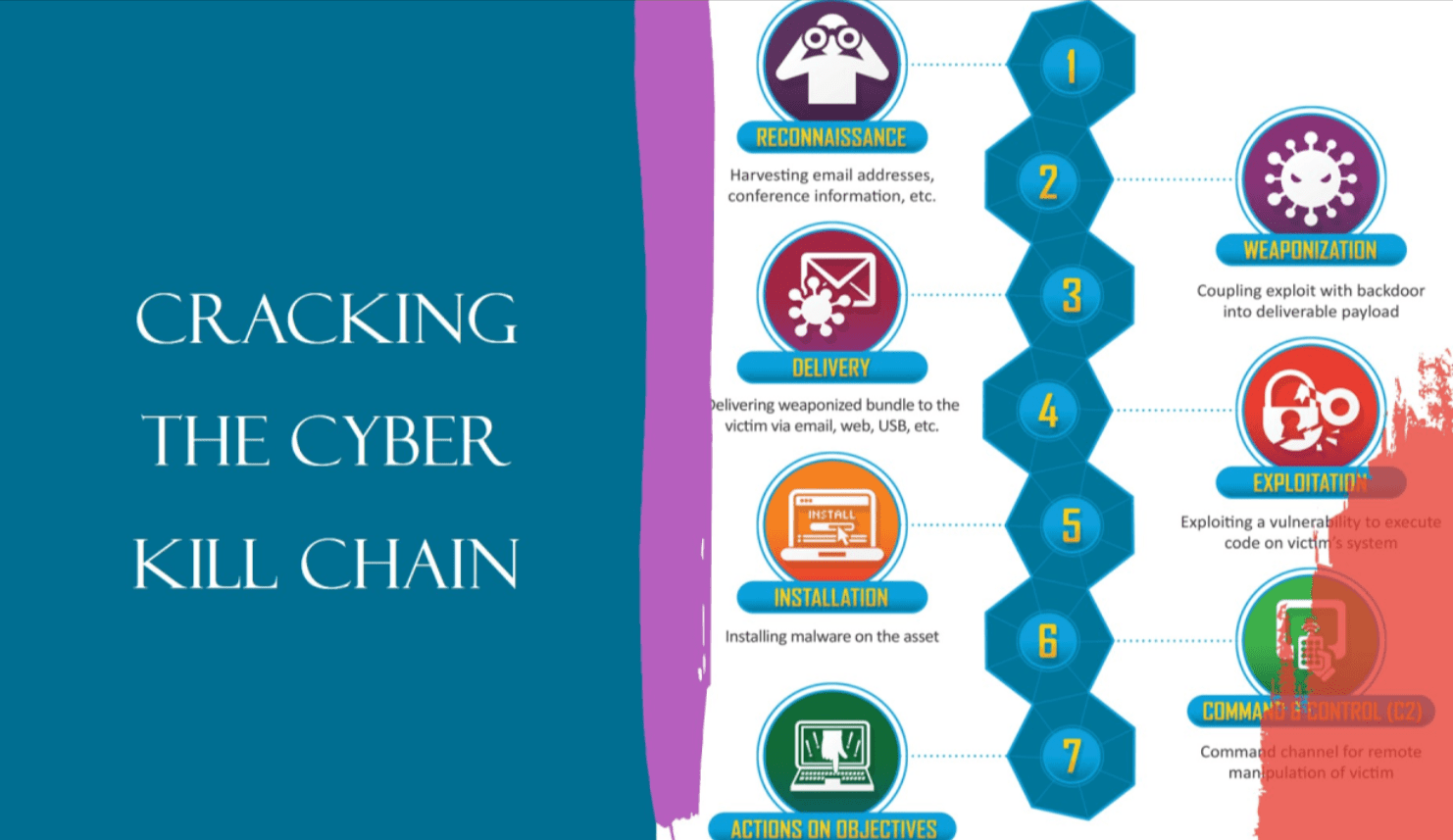
The 7 Steps of the Cyber Kill Chain
Recon (Reconnaissance)
Recon is when a bad guy scopes out a target looking for weak spots like how things are set up or where the target's defenses suck.
Here's a defense tip: Try to keep the private stuff under wraps always be checking your systems, and make sure your team knows about the sneaky tricks hackers use.
Making Weapons
This means the attacker's cooking up some nasty software digital weapons, to mess up the target by hitting where it hurts.
A tip to shield yourself: Keep all your digital stuff up to date and run programs that can spot viruses and other evil software.
Shipping the Bad Stuff
This part's about how the attacker sends over the harmful stuff using tricks like scam emails dodgy websites, or gadgets that are already bugged.
Defense Suggestion: Set up email filters and teach your team how to spot phishing tricks.
Exploitation
Its Nature: When the hacker makes their move, they use weaknesses in the system to get inside.
Defense Suggestion: Don't wait around—update with security fixes fast and watch for weird stuff with intrusion detection gear.
Installation
Its Nature: This is about dropping bad software or gadgets into the system so the bad guys can hang around.
Defense Suggestion: Use software at endpoints to catch and stop nasty programs.
Command and Control (C2)
Its Nature: This is when the baddies set up a way to give orders to the messed-up system from far off.
Defense Trick: Watch for weird patterns in your network flow and cut off chats with bad IPs everyone knows are up to no good.
Actions on Objectives (Exfiltration)
The Lowdown: This is when the baddie wraps up their plan, like swiping files or wrecking your system.
Defense Trick: Set up rules to stop data from leaking and scramble secret info so it's harder to steal.
Boosting Defense with the Cyber Kill Chain
The Cyber Kill Chain isn't just for figuring out attack strategies; it's super useful for beefing up digital guardrails. By knowing every step of an attack, the sec squad can build defenses that work at multiple levels blocking baddies left and right. Let's dive into how this game plan benefits them:
1. Spotting Trouble Sooner
Grasping how an attack unfolds leads to catching the bad guys faster. The security crew zeroes in on hints tied to each phase stepping in before things get worse.
2. Defense With Precision
Instead of just using regular security stuff, the "Cyber Kill Chain" helps companies put up defenses for each part. So, you might use firewalls to stop bad stuff during the delivery part, and then use antivirus programs to block the bad guys during the exploitation bit.
3. Quicker Actions
When you know the attack's phase, you can react fast and in the right way. Take this, like, if the bad dudes have gotten to the installation stage, the good guys can hurry up and get rid of the nasty software to stop more trouble.
4. Keeping the Bad Spread Small
This thing shows how hackers move around in a network. If you break your network into bits and watch it, you can make sure an attack doesn't go everywhere and mess up a lot.
5. Getting Better All the Time
Organizations gain insights from previous attacks with the help of the "Cyber Kill Chain". Security squads scrutinize breached stages post-attack and upgrade their defenses in response.
Beefing Up Security with the "Cyber Kill Chain"
Creating a solid defense tactic means zeroing in on every part of the "Cyber Kill Chain":
Reconnaissance: Start by keeping public info on the down-low, turning off services we don't need, and keeping employee details under wraps.
Weaponization: Make sure to update your software all the time and get those top-notch bad software finders working.
Delivery: Got to have the email blockers, web safety tools, and teach the crew not to fall for those sneaky tricks like phishing.
Exploitation: Get all those weak spots fixed up, and have IDS/IPS ready to catch anyone trying to sneak in.
Installation: Put on some tough endpoint defense programs and scan for bad stuff to keep it from setting up shop.
Command and Control: Keep an eye on the network to spot any fishy chats and shut down those no-good IP addresses we know about.
Actions on Objectives: You gotta encrypt your data and use those DLP gizmos to keep your important info from sneaking out.
Wrap-Up
The "Cyber Kill Chain" forms a foundational study tool to learn and teach about defending against threats that pertain to online crimes. This term is often applied among security professionals in the sense of a way to describe the possible modus operandi of intruders into networks and, thus, how it can be built as armor against every stage of the command as reconnaissance goes up until the moment of data loss.